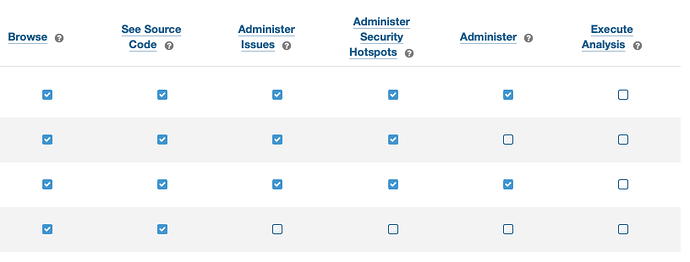
Hello @szallev_raifhu I tried to reproduce your issue on my local environment without luck.
I tried to reproduce with the three types of token available on SonarQube and the result has always been the same.
Test 1 using a squ_ prefixed token.
After creating this token from My Account → Security I verified that both the user and the group associated to my user had the Execute Analysis permission active.
I immediately removed the permission from the user in order to focus on the groups related permissions like you reported.
1st Attempt: usergroup with Global Execute Analysis and Project Execut Analysis → analysis successfully completed 
2nd Attempt: usergroup with Global Execute Analysis and without Project Execut Analysis → analysis successfully completed 
3rd Attempt: usergroup without Global Execute Analysis Permission and with Project Execute Analysis: → analysis successfully completed 
4th Attempt: usergroup without Global Execute Analysis Permission and without Project Execute Analysis: analysis fail as expected 
5th Attempt: usergroup without Global Execute Analysis Permission and with Project Execute Analysis: analysis successfully completed 
6th Attempt: usergroup with Global Execute Analysis Permission and without Project Execute Analysis: analysis successfully completed 
No restarts were done in between, just clicks on the permission selectors on both the project permissions manager and global permission manager
Using the same protocol the test has been done also with tokens of type Project Analysis and Global analysis
Test 2 using a sqp_ prefixed token.
The token got created automatically by the new project wizard
I immediately removed the permission from the user in order to focus on the groups related permissions like you reported.
1st Attempt: usergroup with Global Execute Analysis and Project Execut Analysis → analysis successfully completed 
2nd Attempt: usergroup with Global Execute Analysis and without Project Execut Analysis → analysis successfully completed 
3rd Attempt: usergroup without Global Execute Analysis Permission and with Project Execute Analysis: → analysis successfully completed 
4th Attempt: usergroup without Global Execute Analysis Permission and without Project Execute Analysis: analysis fail as expected 
5th Attempt: usergroup without Global Execute Analysis Permission and with Project Execute Analysis: analysis successfully completed 
6th Attempt: usergroup with Global Execute Analysis Permission and without Project Execute Analysis: analysis successfully completed 
Test 3 using a sqa_ prefixed token.
This is a global analysis token, it can be created by the users with the global Execute Analysis permission.
I immediately removed the permission from the user in order to focus on the groups related permissions like you reported.
1st Attempt: usergroup with Global Execute Analysis and Project Execut Analysis → analysis successfully completed 
2nd Attempt: usergroup with Global Execute Analysis and without Project Execut Analysis → analysis successfully completed 
3rd Attempt: usergroup without Global Execute Analysis Permission and with Project Execute Analysis: → analysis fail as expected 
4th Attempt: usergroup without Global Execute Analysis Permission and without Project Execute Analysis: analysis fail as expected 
5th Attempt: usergroup without Global Execute Analysis Permission and with Project Execute Analysis → analysis fail as expected 
6th Attempt: usergroup with Global Execute Analysis Permission and without Project Execute Analysis: analysis successfully completed 
I think I tested all the possible cases with all the three different type of tokens that can be used for scanning a project.
My SonarQube is running on Mac OS with a Postgres Database, and I would not expect that this can result in a different behavior when adding or removing permissions from a group.
Please let me know if you need more details, or if you can provide more details in order to reproduce your issue.