Hello SonarSource Support,
We are testing SonarQube Server Enterprise with the WebGoat project, specifically the taint analysis.
The two relevant files are:
-
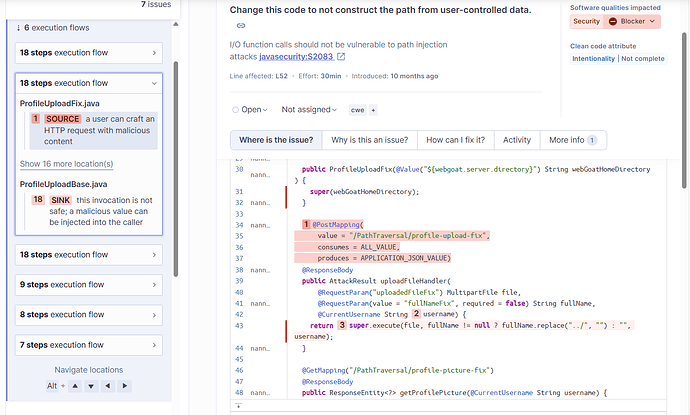
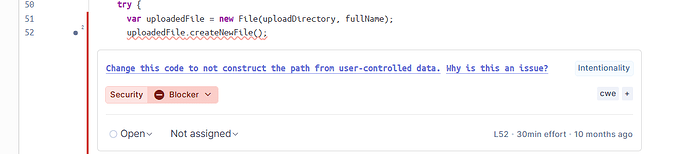
ProfileUploadBase.java(uses the user-controlled parameter directly in aFileconstructor) -
ProfileUploadFix.java(applies.replace("../", "")to the input before passing it along)
Expectation:
According to the Java security rules, I expected SonarQube to report a taint analysis issue ( rule S2083) for ProfileUploadBase.java. I also expected to see the taint flow in the UI (SOURCE → propagation → SINK).
Observation:
-
No taint analysis issues are reported for these files (or any files in this repo) in our scan.
-
I confirmed that rule javasecurity:S2083 is active in the Java Quality Profile assigned to the project (we are using the default Java profile) + I enabled the debug for scan and noticed this rule is active for Java.
Questions:
-
Is it expected that WebGoat repo don’t have any taint analysis in this demo?
-
Do we need to use Security Engine Custom Configuration in order to detect these flows, or should SonarQube detect them automatically?
-
Are there any additional configuration steps required to ensure taint analysis results (execution flows) are displayed in the UI?
Thanks,