JaspervdM80
August 15, 2023, 12:13pm
1
Hi,
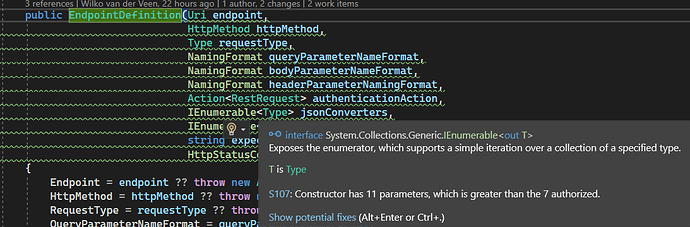
In our Sonarcloud environment the S107 warning is not triggered, while Visual Studio (in connected mode) does show a warning.
I have checked if the rule is disabled in Quality Profile or that the issue is marked with wont fix or any other tag.
Is there any way we can validate why the rule is not triggered?
Kind Regards Jasper
(ps just to be clear, the quality gate should fail on this issue)
Colin
August 15, 2023, 12:21pm
2
Hey there.
What version of Visual Studio / MSBuild are you using?
JaspervdM80
August 15, 2023, 12:28pm
3
Hi,
Thanks for the reply.
Visual Studio 2022 17.6.4
But Visual Studio is showing the issue correctly, SonarCloud does not trigger this issue.
Colin
August 21, 2023, 8:34am
4
Thanks. I was asking because we became aware of an issue with a version of Visual Studio where not-default rules stopped being reported .
Do you have maybe different configuration files for analysis between debug and release modes (such files are editorconfig, global configuration files, or ruleset files)?
JaspervdM80
August 21, 2023, 8:49am
5
Hi Colin,
Thanks for replying, but as I tried to mention. Visual Studio is showing rules correctly in connected mode.
If I run a pipeline with sonar-scanner it does not trigger the issue, as SonarCloud does not show the mentioned issue (and more issues).
Visual Studio (CORRECTLY)
Sonar Cloud (NOT CORRECT)
What could be the cause of this?
Colin
August 21, 2023, 9:13am
6
Thanks. I understand the issue. I cannot reproduce it.
Here is a repo mimicking your reproducer: SonarCloud
With the correct issue raised: SonarCloud
And for good measure, here’s the issue raised in the context of the .NET Build: Create main.yml · colin-sonarsource/S107Test@47c9505 · GitHub
There could be some issue exclusions set in some non-obvious places. Can you retreive the SonarScanner context by going to your project Administration > Background Tasks ?
JaspervdM80
August 21, 2023, 9:19am
7
This is the context log
SonarCloud plugins:
- IaC Code Quality and Security 1.19.0.5623 (iac)
- PL/SQL Code Quality and Security 3.9.0.5181 (plsql)
- Scala Code Quality and Security 1.13.0.4374 (sonarscala)
- C# Code Quality and Security 9.7.0.75501 (csharp)
- Vulnerability Analysis 10.2.0-M2.21972 (security)
- Java Code Quality and Security 7.23.0.32023 (java)
- HTML Code Quality and Security 3.8.0.3510 (web)
- Flex Code Quality and Security 2.9.0.3375 (flex)
- XML Code Quality and Security 2.9.0.4055 (xml)
- Text Code Quality and Security 2.2.0.1571 (text)
- VB.NET Code Quality and Security 9.7.0.75501 (vbnet)
- Swift Code Quality and Security 4.9.0.5915 (swift)
- CFamily Code Quality and Security 6.47.0.62356 (cpp)
- Python Code Quality and Security 4.6.0.12071 (python)
- Dataflow Bug Detection Rules for Python 1.16.0.4300 (dbdpythonfrontend)
- Dataflow Bug Detection 1.16.0.4300 (dbd)
- Go Code Quality and Security 1.13.0.4374 (go)
- JaCoCo 1.3.0.1538 (jacoco)
- Kotlin Code Quality and Security 2.16.0.2832 (kotlin)
- Dataflow Bug Detection Rules for Java 1.16.0.4300 (dbdjavafrontend)
- T-SQL Code Quality and Security 1.9.0.5692 (tsql)
- Apex Code Quality and Security 1.13.0.4374 (sonarapex)
- JavaScript/TypeScript/CSS Code Quality and Security 10.4.0.22160 (javascript)
- Ruby Code Quality and Security 1.13.0.4374 (ruby)
- Vulnerability Rules for C# 10.2.0-M2.21972 (securitycsharpfrontend)
- Vulnerability Rules for Java 10.2.0-M2.21972 (securityjavafrontend)
- License for SonarLint 8.0.0.45216 (license)
- Vulnerability Rules for JS 10.2.0-M2.21972 (securityjsfrontend)
- COBOL Code Quality 5.4.0.6318 (cobol)
- Vulnerability Rules for Python 10.2.0-M2.21972 (securitypythonfrontend)
- PHP Code Quality and Security 3.30.0.9766 (php)
- ABAP Code Quality and Security 3.12.0.4303 (abap)
- Configuration detection fot Code Quality and Security 1.2.0.267 (config)
- Vulnerability Rules for PHP 10.2.0-M2.21972 (securityphpfrontend)
Project server settings:
- sonar.pullrequest.provider=Azure DevOps Services
- sonar.pullrequest.vsts.token.secured=******
- sonar.sensor.cache.project.enable=false
Project scanner properties:
- sonar.branch.name=azure-pipelines/pool2
- sonar.coverage.exclusions=**/example*/**,**/*.generated.*, **/App_Plugins/**, **/?mbraco/**, **/jquery*.js, **/moment*.js, **/bootstrap*.js, **/Attributes/Foolproof/**, **/vue*.js, **/fontawesome.*/**, **/Models/Generated/**, **/webpack.*.js,**/*.cshtml
- sonar.cpd.exclusions=**/*.cshtml
- sonar.cs.opencover.reportsPaths=D:\DFN_BuildAgent_2\_work\_temp/**/coverage.opencover.xml
- sonar.cs.vstest.reportsPaths=D:\DFN_BuildAgent_2\_work\_temp/**/*.trx
- sonar.exclusions=**/example*/**,**/*.generated.*, **/App_Plugins/**, **/?mbraco/**, **/jquery*.js, **/moment*.js, **/bootstrap*.js, **/Attributes/Foolproof/**, **/vue*.js, **/fontawesome.*/**, **/Models/Generated/**, **/webpack.*.js
- sonar.host.url=https://sonarcloud.io/
- sonar.modules=91135346-02DC-4229-BB64-CED290F4B173
- sonar.organization=deltafibernl
- sonar.projectBaseDir=D:\DFN_BuildAgent_2\_work\282\s
- sonar.projectKey=net.deltafibernl_test-project
- sonar.projectName=Test Project
- sonar.projectVersion=1.0
- sonar.pullrequest.cache.basepath=D:\DFN_BuildAgent_2\_work\282\s
- sonar.scanAllFiles=true
- sonar.scanner.app=ScannerMSBuild
- sonar.scanner.appVersion=5.13
- sonar.scanner.metadataFilePath=D:\DFN_BuildAgent_2\_work\_temp\sonar\64764\e63f1317-361f-1637-c0d8-58b287ac17ba\report-task.txt
- sonar.sourceEncoding=windows-1252
- sonar.token=******
- sonar.visualstudio.enable=false
- sonar.working.directory=D:\DFN_BuildAgent_2\_work\282\.sonarqube\out\.sonar
Scanner properties of module: net.deltafibernl_test-project:net.deltafibernl_test-project:91135346-02DC-4229-BB64-CED290F4B173
- sonar.cs.analyzer.projectOutPaths="D:\DFN_BuildAgent_2\_work\282\.sonarqube\out\0"
- sonar.cs.roslyn.reportFilePaths="D:\DFN_BuildAgent_2\_work\282\.sonarqube\out\0\Issues.json"
- sonar.moduleKey=net.deltafibernl_test-project:net.deltafibernl_test-project:91135346-02DC-4229-BB64-CED290F4B173
- sonar.projectBaseDir=D:\DFN_BuildAgent_2\_work\282\s\source
- sonar.projectKey=net.deltafibernl_test-project:net.deltafibernl_test-project:91135346-02DC-4229-BB64-CED290F4B173
- sonar.projectName=TestProject
- sonar.sourceEncoding=utf-8
- sonar.sources="D:\DFN_BuildAgent_2\_work\282\s\source\Program.cs"
- sonar.working.directory=D:\DFN_BuildAgent_2\_work\282\.sonarqube\out\.sonar\mod0
Colin
August 22, 2023, 9:00am
8
No smoking gun there…
Can I suggest sharing the full build/analysis logs of this test project?
Share the Scanner for .NET verbose logs
Add /d:"sonar.verbose=true" to the…
SonarScanner.MSBuild.exe or dotnet sonarscanner begin command to get more detailed logs
For example: SonarScanner.MSBuild.exe begin /k:"MyProject" /d:"sonar.verbose=true"
“SonarQubePrepare” or “SonarCloudPrepare” task’s extraProperties argument if you are using Azure DevOps
The important logs are in the END step (i.e. SonarQubeAnalyze / SonarCloudAnalyze / “Run Code Analysis”)
Share the msbuild detailed logs
MsBuild.exe /t:Rebuild /v:d
or
dotnet build -v:d
JaspervdM80
August 23, 2023, 7:41am
9
This is the detailed Azure Devops Log:AzureDevopsLog.zip (1.0 MB)
This is the localbuild log:localbuild.zip (41.8 KB)
Colin
August 23, 2023, 7:58am
10
It looks like your build logs don’t include anything related to SonarCloud (running the analyzers). Can you get the detailed logs from your build and share those?
JaspervdM80
August 24, 2023, 8:29am
11
I misunderstood, I thought you only needed the local build logs.
localsonarcloud.zip (2.0 MB)
these are the local issues:Issues.zip (1.5 KB)
Colin
August 24, 2023, 12:00pm
12
This is still only the output from the SonarScanner, not the actual build (MSBuild.exe or dotnet)
JaspervdM80
August 24, 2023, 12:15pm
13
Sorry I am completely lost a what you are requesting:
You requested the msbuild logs, but do i understand correctly now, you want the msbuild logs after the analyzers have been loaded?
Please keep in mind that running the sonnar scanner locally is not what most users do.
this is the local build with analyzers?localbuild.log (826.2 KB)