We have a translation module that takes on the PHP backend a string and checks in a json file the mapped translated value. Regretfully Sonar marks all these translation lookups as a vulnerability, it will be a lot of work to try and manually override these vulnerabilities/false positives. Is there anything you can do about it?
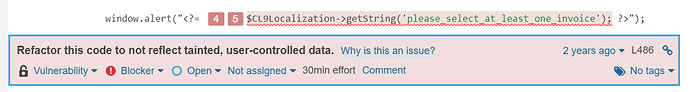
Btw when I open this file seperately it doens’t show this as a security issue, only when other files are calling this function its highlighted as: Refactor this code to not reflect tainted, user-controlled data.
Moreover the exact same code in the our other repo does not highlight this as a security issue.
Hey Jim,
I am sorry to hear that! Would it be possible to share the code of this file and the one calling it, or the full stack-trace? Thanks! This would help us a lot to see what is going on.
Well it is a private repo, so not on the public forum, the code in question including file name is in the screenshot though.
“Refactor this code to not reflect tainted, user-controlled data.” means it is detected as a Cross-Site Scripting vulnerability, thus I am thinking that something happens after 3 (for example, it ends up in an echo).
Judging from the screenshot it looks to me that step 1 actually returns user input (Joomla\Input\Input::getString), so the problem likely occurs after step 3.
I agree with your statement fully that that gets it from the input, but in order to make it clear let me share 4,5
It actually calls the localization class and then for some reason links the localization class to the securization class. The localization class only looks up a string in a file, the securization class which is not invoked here indeed gets filtered inputs from the joomla frontend.
Thanks a lot, Jim! It makes more sense now, it looks like a type inference problem. I will have to talk to developers, I will come back to you.
There does not seem to be a clean way to solve it at the moment but we are working on this problem and hopefully will be able to improve it soon! For now I would recommend to exclude the file Securization.php from the analysis to prevent this false-positive.