Hi All,
We have a Azure DevOPS Release Pipeline Integrated with SonarCloud.
First we prepare SonarCloud analysis configuration, then we run scanner and upload the results to the SonarCloud server, and finally we Publish SonarCloud’s Quality Gate result on the Azure Pipelines build result (to be used after the actual analysis).
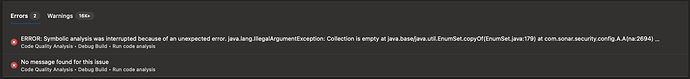
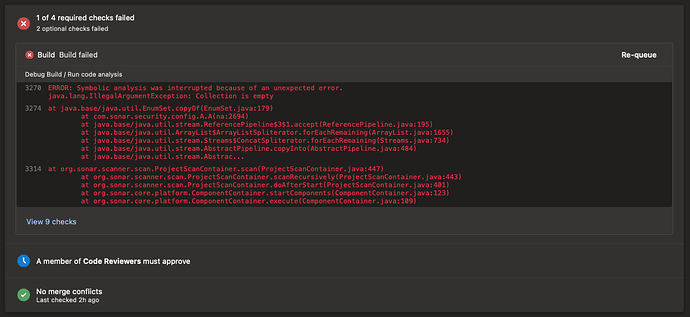
We are getting below error on the ’ Run Code Analysis’ step (Step#2). This started 09/15.
Has anyone come across this error?
The Background Task Id is either AXv1ijg83OcDDGD_HQaj OR AXv5l2Hti8PvPOU9jm-b. When I try to see the warning message, I get this: Symbolic analysis was interrupted because of an unexpected error.
2021-09-18T15:47:11.1404435Z 15:47:10.772 DEBUG: Resource file jssecurity/encoders/common.json was not read
2021-09-18T15:47:11.1723178Z 15:47:10.772 DEBUG: Resource file jssecurity/encoders/S2076.json was not read
2021-09-18T15:47:11.1724729Z 15:47:10.772 DEBUG: Resource file jssecurity/encoders/S2078.json was not read
2021-09-18T15:47:11.1725694Z 15:47:10.772 DEBUG: Resource file jssecurity/encoders/S2083.json was not read
2021-09-18T15:47:11.1726508Z 15:47:10.772 DEBUG: Resource file jssecurity/encoders/S2091.json was not read
2021-09-18T15:47:11.1925608Z 15:47:10.772 DEBUG: Resource file jssecurity/encoders/S2631.json was not read
2021-09-18T15:47:11.1947804Z 15:47:10.772 DEBUG: Resource file jssecurity/encoders/S3649.json was not read
2021-09-18T15:47:11.1948721Z 15:47:10.772 DEBUG: Resource file jssecurity/encoders/S5131.json was not read
2021-09-18T15:47:11.1949616Z 15:47:10.772 DEBUG: Resource file jssecurity/encoders/S5135.json was not read
2021-09-18T15:47:11.1950451Z 15:47:10.772 DEBUG: Resource file jssecurity/encoders/S5144.json was not read
2021-09-18T15:47:11.1961912Z 15:47:10.772 DEBUG: Resource file jssecurity/encoders/S5145.json was not read
2021-09-18T15:47:11.1962758Z 15:47:10.772 DEBUG: Resource file jssecurity/encoders/S5146.json was not read
2021-09-18T15:47:11.1963550Z 15:47:10.772 DEBUG: Resource file jssecurity/encoders/S5147.json was not read
2021-09-18T15:47:11.1964321Z 15:47:10.772 DEBUG: Resource file jssecurity/encoders/S5167.json was not read
2021-09-18T15:47:11.1991074Z 15:47:10.772 DEBUG: Resource file jssecurity/encoders/S5334.json was not read
2021-09-18T15:47:11.1992179Z 15:47:10.774 DEBUG: Resource file jssecurity/encoders/S5335.json was not read
2021-09-18T15:47:11.2003842Z 15:47:10.775 DEBUG: Resource file jssecurity/encoders/S5696.json was not read
2021-09-18T15:47:11.2004815Z 15:47:10.775 DEBUG: Resource file jssecurity/encoders/S5883.json was not read
2021-09-18T15:47:11.2183321Z 15:47:10.775 DEBUG: Resource file jssecurity/encoders/S6096.json was not read
2021-09-18T15:47:11.2306342Z 15:47:10.775 DEBUG: Resource file jssecurity/encoders/S6105.json was not read
2021-09-18T15:47:11.2307146Z 15:47:10.775 DEBUG: loaded 0 encoders.
2021-09-18T15:47:11.2457703Z 15:47:10.775 DEBUG: Resource file jssecurity/decoders/common.json was not read
2021-09-18T15:47:11.2554344Z ##[error]15:47:10.784 ERROR: Symbolic analysis was interrupted because of an unexpected error.
java.lang.IllegalArgumentException: Collection is empty
at java.base/java.util.EnumSet.copyOf(EnumSet.java:179)
at com.sonar.security.config.A.A(na:2694)
at java.base/java.util.stream.ReferencePipeline$3$1.accept(ReferencePipeline.java:195)
at java.base/java.util.ArrayList$ArrayListSpliterator.forEachRemaining(ArrayList.java:1655)
at java.base/java.util.stream.Streams$ConcatSpliterator.forEachRemaining(Streams.java:734)
at java.base/java.util.stream.AbstractPipeline.copyInto(AbstractPipeline.java:484)
at java.base/java.util.stream.AbstractPipeline.wrapAndCopyInto(AbstractPipeline.java:474)
at java.base/java.util.stream.ReduceOps$ReduceOp.evaluateSequential(ReduceOps.java:913)
at java.base/java.util.stream.AbstractPipeline.evaluate(AbstractPipeline.java:234)
at java.base/java.util.stream.ReferencePipeline.collect(ReferencePipeline.java:578)
at com.sonar.security.config.A.A(na:1695)
at com.sonar.security.rules.J.D(na:150)
at com.sonar.security.E.executeChecks(na:3244)
at com.sonar.security.E.execute(na:1193)
at org.sonar.scanner.sensor.AbstractSensorWrapper.analyse(AbstractSensorWrapper.java:45)
at org.sonar.scanner.sensor.ModuleSensorsExecutor.execute(ModuleSensorsExecutor.java:75)
at org.sonar.scanner.sensor.ModuleSensorsExecutor.execute(ModuleSensorsExecutor.java:51)
at org.sonar.scanner.scan.ModuleScanContainer.doAfterStart(ModuleScanContainer.java:68)
at org.sonar.core.platform.ComponentContainer.startComponents(ComponentContainer.java:123)
at org.sonar.core.platform.ComponentContainer.execute(ComponentContainer.java:109)
at org.sonar.scanner.scan.ProjectScanContainer.scan(ProjectScanContainer.java:445)
at org.sonar.scanner.scan.ProjectScanContainer.scanRecursively(ProjectScanContainer.java:441)
at org.sonar.scanner.scan.ProjectScanContainer.doAfterStart(ProjectScanContainer.java:399)
at org.sonar.core.platform.ComponentContainer.startComponents(ComponentContainer.java:123)
at org.sonar.core.platform.ComponentContainer.execute(ComponentContainer.java:109)
at org.sonar.scanner.bootstrap.GlobalContainer.doAfterStart(GlobalContainer.java:128)
at org.sonar.core.platform.ComponentContainer.startComponents(ComponentContainer.java:123)
at org.sonar.core.platform.ComponentContainer.execute(ComponentContainer.java:109)
at org.sonar.batch.bootstrapper.Batch.doExecute(Batch.java:58)
at org.sonar.batch.bootstrapper.Batch.execute(Batch.java:52)
at org.sonarsource.scanner.api.internal.batch.BatchIsolatedLauncher.execute(BatchIsolatedLauncher.java:46)
at java.base/jdk.internal.reflect.NativeMethodAccessorImpl.invoke0(Native Method)
at java.base/jdk.internal.reflect.NativeMethodAccessorImpl.invoke(NativeMethodAccessorImpl.java:62)
at java.base/jdk.internal.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43)
at java.base/java.lang.reflect.Method.invoke(Method.java:566)
at org.sonarsource.scanner.api.internal.IsolatedLauncherProxy.invoke(IsolatedLauncherProxy.java:60)
at com.sun.proxy.$Proxy0.execute(Unknown Source)
at org.sonarsource.scanner.api.EmbeddedScanner.doExecute(EmbeddedScanner.java:189)
at org.sonarsource.scanner.api.EmbeddedScanner.execute(EmbeddedScanner.java:138)
at org.sonarsource.scanner.cli.Main.execute(Main.java:112)
at org.sonarsource.scanner.cli.Main.execute(Main.java:75)
at org.sonarsource.scanner.cli.Main.main(Main.java:61)
2021-09-18T15:47:11.2599381Z ##[debug]Processed: ##vso[task.logissue type=error;]15:47:10.784 ERROR: Symbolic analysis was interrupted because of an unexpected error.%0D%0Ajava.lang.IllegalArgumentException: Collection is empty%0D%0A at java.base/java.util.EnumSet.copyOf(EnumSet.java:179)%0D%0A at com.sonar.security.config.A.A(na:2694)%0D%0A at java.base/java.util.stream.ReferencePipeline$3$1.accept(ReferencePipeline.java:195)%0D%0A at java.base/java.util.ArrayList$ArrayListSpliterator.forEachRemaining(ArrayList.java:1655)%0D%0A at java.base/java.util.stream.Streams$ConcatSpliterator.forEachRemaining(Streams.java:734)%0D%0A at java.base/java.util.stream.AbstractPipeline.copyInto(AbstractPipeline.java:484)%0D%0A at java.base/java.util.stream.AbstractPipeline.wrapAndCopyInto(AbstractPipeline.java:474)%0D%0A at java.base/java.util.stream.ReduceOps$ReduceOp.evaluateSequential(ReduceOps.java:913)%0D%0A at java.base/java.util.stream.AbstractPipeline.evaluate(AbstractPipeline.java:234)%0D%0A at java.base/java.util.stream.ReferencePipeline.collect(ReferencePipeline.java:578)%0D%0A at com.sonar.security.config.A.A(na:1695)%0D%0A at com.sonar.security.rules.J.D(na:150)%0D%0A at com.sonar.security.E.executeChecks(na:3244)%0D%0A at com.sonar.security.E.execute(na:1193)%0D%0A at org.sonar.scanner.sensor.AbstractSensorWrapper.analyse(AbstractSensorWrapper.java:45)%0D%0A at org.sonar.scanner.sensor.ModuleSensorsExecutor.execute(ModuleSensorsExecutor.java:75)%0D%0A at org.sonar.scanner.sensor.ModuleSensorsExecutor.execute(ModuleSensorsExecutor.java:51)%0D%0A at org.sonar.scanner.scan.ModuleScanContainer.doAfterStart(ModuleScanContainer.java:68)%0D%0A at org.sonar.core.platform.ComponentContainer.startComponents(ComponentContainer.java:123)%0D%0A at org.sonar.core.platform.ComponentContainer.execute(ComponentContainer.java:109)%0D%0A at org.sonar.scanner.scan.ProjectScanContainer.scan(ProjectScanContainer.java:445)%0D%0A at org.sonar.scanner.scan.ProjectScanContainer.scanRecursively(ProjectScanContainer.java:441)%0D%0A at org.sonar.scanner.scan.ProjectScanContainer.doAfterStart(ProjectScanContainer.java:399)%0D%0A at org.sonar.core.platform.ComponentContainer.startComponents(ComponentContainer.java:123)%0D%0A at org.sonar.core.platform.ComponentContainer.execute(ComponentContainer.java:109)%0D%0A at org.sonar.scanner.bootstrap.GlobalContainer.doAfterStart(GlobalContainer.java:128)%0D%0A at org.sonar.core.platform.ComponentContainer.startComponents(ComponentContainer.java:123)%0D%0A at org.sonar.core.platform.ComponentContainer.execute(ComponentContainer.java:109)%0D%0A at org.sonar.batch.bootstrapper.Batch.doExecute(Batch.java:58)%0D%0A at org.sonar.batch.bootstrapper.Batch.execute(Batch.java:52)%0D%0A at org.sonarsource.scanner.api.internal.batch.BatchIsolatedLauncher.execute(BatchIsolatedLauncher.java:46)%0D%0A at java.base/jdk.internal.reflect.NativeMethodAccessorImpl.invoke0(Native Method)%0D%0A at java.base/jdk.internal.reflect.NativeMethodAccessorImpl.invoke(NativeMethodAccessorImpl.java:62)%0D%0A at java.base/jdk.internal.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43)%0D%0A at java.base/java.lang.reflect.Method.invoke(Method.java:566)%0D%0A at org.sonarsource.scanner.api.internal.IsolatedLauncherProxy.invoke(IsolatedLauncherProxy.java:60)%0D%0A at com.sun.proxy.$Proxy0.execute(Unknown Source)%0D%0A at org.sonarsource.scanner.api.EmbeddedScanner.doExecute(EmbeddedScanner.java:189)%0D%0A at org.sonarsource.scanner.api.EmbeddedScanner.execute(EmbeddedScanner.java:138)%0D%0A at org.sonarsource.scanner.cli.Main.execute(Main.java:112)%0D%0A at org.sonarsource.scanner.cli.Main.execute(Main.java:75)%0D%0A at org.sonarsource.scanner.cli.Main.main(Main.java:61)
2021-09-18T15:47:11.2626420Z 15:47:10.784 ERROR: Symbolic analysis was interrupted because of an unexpected error.
2021-09-18T15:47:11.2627339Z java.lang.IllegalArgumentException: Collection is empty
2021-09-18T15:47:11.2628017Z at java.base/java.util.EnumSet.copyOf(EnumSet.java:179)
2021-09-18T15:47:11.2632028Z at com.sonar.security.config.A.A(na:2694)
2021-09-18T15:47:11.2632783Z at java.base/java.util.stream.ReferencePipeline$3$1.accept(ReferencePipeline.java:195)
2021-09-18T15:47:11.2635275Z at java.base/java.util.ArrayList$ArrayListSpliterator.forEachRemaining(ArrayList.java:1655)
2021-09-18T15:47:11.2636147Z at java.base/java.util.stream.Streams$ConcatSpliterator.forEachRemaining(Streams.java:734)
2021-09-18T15:47:11.2636900Z at java.base/java.util.stream.AbstractPipeline.copyInto(AbstractPipeline.java:484)
2021-09-18T15:47:11.2637636Z at java.base/java.util.stream.AbstractPipeline.wrapAndCopyInto(AbstractPipeline.java:474)
2021-09-18T15:47:11.2642090Z at java.base/java.util.stream.ReduceOps$ReduceOp.evaluateSequential(ReduceOps.java:913)
2021-09-18T15:47:11.2643124Z at java.base/java.util.stream.AbstractPipeline.evaluate(AbstractPipeline.java:234)
2021-09-18T15:47:11.2643893Z at java.base/java.util.stream.ReferencePipeline.collect(ReferencePipeline.java:578)
2021-09-18T15:47:11.2644535Z at com.sonar.security.config.A.A(na:1695)
2021-09-18T15:47:11.2645104Z at com.sonar.security.rules.J.D(na:150)
2021-09-18T15:47:11.2645676Z at com.sonar.security.E.executeChecks(na:3244)
2021-09-18T15:47:11.2646255Z at com.sonar.security.E.execute(na:1193)
2021-09-18T15:47:11.2646920Z at org.sonar.scanner.sensor.AbstractSensorWrapper.analyse(AbstractSensorWrapper.java:45)
2021-09-18T15:47:11.2647679Z at org.sonar.scanner.sensor.ModuleSensorsExecutor.execute(ModuleSensorsExecutor.java:75)
2021-09-18T15:47:11.2648435Z at org.sonar.scanner.sensor.ModuleSensorsExecutor.execute(ModuleSensorsExecutor.java:51)
2021-09-18T15:47:11.2652078Z at org.sonar.scanner.scan.ModuleScanContainer.doAfterStart(ModuleScanContainer.java:68)
2021-09-18T15:47:11.2652876Z at org.sonar.core.platform.ComponentContainer.startComponents(ComponentContainer.java:123)
2021-09-18T15:47:11.2655383Z at org.sonar.core.platform.ComponentContainer.execute(ComponentContainer.java:109)
2021-09-18T15:47:11.2656329Z at org.sonar.scanner.scan.ProjectScanContainer.scan(ProjectScanContainer.java:445)
2021-09-18T15:47:11.2657100Z at org.sonar.scanner.scan.ProjectScanContainer.scanRecursively(ProjectScanContainer.java:441)
2021-09-18T15:47:11.2658063Z at org.sonar.scanner.scan.ProjectScanContainer.doAfterStart(ProjectScanContainer.java:399)
2021-09-18T15:47:11.2658894Z at org.sonar.core.platform.ComponentContainer.startComponents(ComponentContainer.java:123)
2021-09-18T15:47:11.2659693Z at org.sonar.core.platform.ComponentContainer.execute(ComponentContainer.java:109)
2021-09-18T15:47:11.2660457Z at org.sonar.scanner.bootstrap.GlobalContainer.doAfterStart(GlobalContainer.java:128)
2021-09-18T15:47:11.2661237Z at org.sonar.core.platform.ComponentContainer.startComponents(ComponentContainer.java:123)
2021-09-18T15:47:11.2662003Z at org.sonar.core.platform.ComponentContainer.execute(ComponentContainer.java:109)
2021-09-18T15:47:11.2662843Z at org.sonar.batch.bootstrapper.Batch.doExecute(Batch.java:58)
2021-09-18T15:47:11.2663500Z at org.sonar.batch.bootstrapper.Batch.execute(Batch.java:52)
2021-09-18T15:47:11.2664246Z at org.sonarsource.scanner.api.internal.batch.BatchIsolatedLauncher.execute(BatchIsolatedLauncher.java:46)
2021-09-18T15:47:11.2665027Z at java.base/jdk.internal.reflect.NativeMethodAccessorImpl.invoke0(Native Method)
2021-09-18T15:47:11.2665764Z at java.base/jdk.internal.reflect.NativeMethodAccessorImpl.invoke(NativeMethodAccessorImpl.java:62)
2021-09-18T15:47:11.2666578Z at java.base/jdk.internal.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43)
2021-09-18T15:47:11.2667305Z at java.base/java.lang.reflect.Method.invoke(Method.java:566)
2021-09-18T15:47:11.2668024Z at org.sonarsource.scanner.api.internal.IsolatedLauncherProxy.invoke(IsolatedLauncherProxy.java:60)
2021-09-18T15:47:11.2668705Z at com.sun.proxy.$Proxy0.execute(Unknown Source)
2021-09-18T15:47:11.2669419Z at org.sonarsource.scanner.api.EmbeddedScanner.doExecute(EmbeddedScanner.java:189)
2021-09-18T15:47:11.2670156Z at org.sonarsource.scanner.api.EmbeddedScanner.execute(EmbeddedScanner.java:138)
2021-09-18T15:47:11.2670840Z at org.sonarsource.scanner.cli.Main.execute(Main.java:112)
2021-09-18T15:47:11.2671491Z at org.sonarsource.scanner.cli.Main.execute(Main.java:75)
2021-09-18T15:47:11.2672126Z at org.sonarsource.scanner.cli.Main.main(Main.java:61)
2021-09-18T15:47:11.2672452Z
2021-09-18T15:47:11.2672983Z 15:47:10.775 DEBUG: Resource file jssecurity/decoders/S2076.json was not read
2021-09-18T15:47:11.2673656Z 15:47:10.779 DEBUG: Resource file jssecurity/decoders/S2078.json was not read
2021-09-18T15:47:11.2674322Z 15:47:10.779 DEBUG: Resource file jssecurity/decoders/S2083.json was not read
2021-09-18T15:47:11.2674985Z 15:47:10.779 DEBUG: Resource file jssecurity/decoders/S2091.json was not read
2021-09-18T15:47:11.2675647Z 15:47:10.779 DEBUG: Resource file jssecurity/decoders/S2631.json was not read
2021-09-18T15:47:11.2684222Z 15:47:10.779 DEBUG: Resource file jssecurity/decoders/S3649.json was not read
2021-09-18T15:47:11.2688704Z 15:47:10.779 DEBUG: Resource file jssecurity/decoders/S5131.json was not read
2021-09-18T15:47:11.2693006Z 15:47:10.779 DEBUG: Resource file jssecurity/decoders/S5135.json was not read
2021-09-18T15:47:11.2693801Z 15:47:10.779 DEBUG: Resource file jssecurity/decoders/S5144.json was not read
2021-09-18T15:47:11.2697077Z 15:47:10.780 DEBUG: Resource file jssecurity/decoders/S5145.json was not read
2021-09-18T15:47:11.2697915Z 15:47:10.780 DEBUG: Resource file jssecurity/decoders/S5146.json was not read
2021-09-18T15:47:11.2698591Z 15:47:10.780 DEBUG: Resource file jssecurity/decoders/S5147.json was not read