Hello Community,
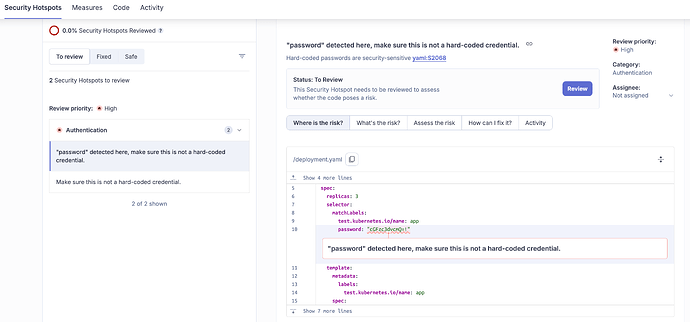
We’re excited to announce a significant enhancement to our secret detection capabilities: Sonar now analyzes YAML and JSON files for leaked secrets!
The Problem
YAML and JSON files are widely used to configure and deliver software. It’s easy to accidentally paste a secret into these files, which can then be pushed to your repository.
The Solution
Sonar’s analysis engine now scans YAML and JSON files to detect leaked secrets.
How to Use
Because YAML and JSON files are very common, this feature is not activated by default. You can enable it on demand by setting the following properties:
sonar.yaml.activate=true
sonar.json.activate=true
Once these properties are provided to the Scanner, YAML and JSON files will be included in the analysis, currently only when using the Scanner CLI. We are working to update our other Scanners to support this feature seamlessly.
Subscription Impact:
Because Sonar now scans YAML and JSON files, the lines of code (LOCs) in these files will be counted and will contribute to the total LOCs consumed under your subscription.
This enhancement is available now on SonarQube Cloud. We encourage you to run a fresh analysis on your projects to benefit from this extra level of protection.
Enjoy!
Alex