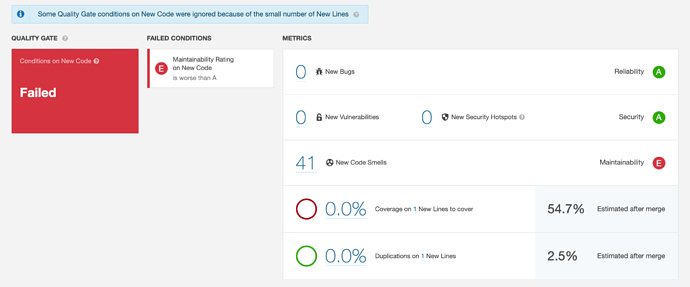
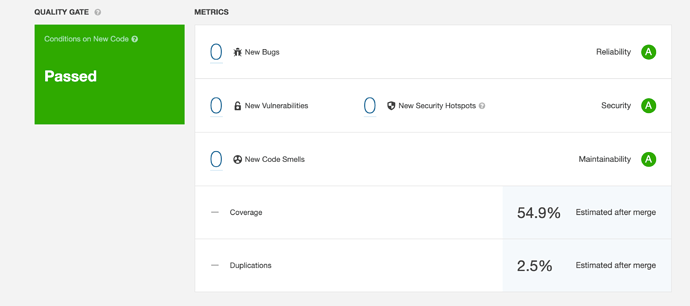
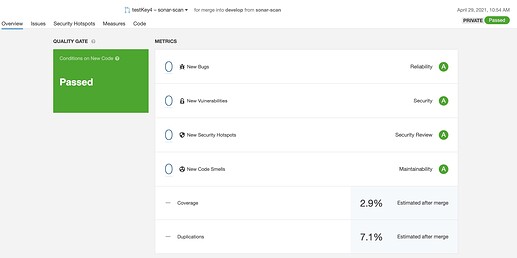
So I am scanning a Java pull request on GitHub with AWS CodeBuild for CI using sonar-scanner-4.4.0.2170-linux and it is not publishing analysis on new lines to SonarCloud PR.
Scanner command used:
sonar-scanner \
-Dsonar.pullrequest.base=spike/test-base-branch \
-Dsonar.pullrequest.branch=spike/test-pr-branch \
-Dsonar.pullrequest.key=*** \
-Dsonar.pullrequest.provider=github \
-Dsonar.pullrequest.github.repository=*** \
-Dsonar.coverage.jacoco.xmlReportPaths=build/reports/coverage/jacoco.xml \
-Dsonar.projectKey=*** \
-Dsonar.projectName=*** \
-Dsonar.organization=*** \
-Dsonar.sources=src \
-Dsonar.host.url=https://sonarcloud.io \
-Dsonar.sourceEncoding=UTF-8 \
-Dsonar.login=*** \
-Dsonar.java.source=1.8 \
-Dsonar.java.binaries=build/classes \
-Dsonar.java.libraries=build/native-libs \
-Dsonar.scm.provider=git \
-Dsonar.scm.exclusions.disabled=true
Output:
INFO: Scanner configuration file: /codebuild/output/src495061989/src/github.com/***/sonar-scanner-4.4.0.2170-linux/conf/sonar-scanner.properties
INFO: Project root configuration file: /codebuild/output/src495061989/src/github.com/***/sonar-project.properties
INFO: SonarScanner 4.4.0.2170
INFO: Java 11.0.3 AdoptOpenJDK (64-bit)
INFO: Linux 4.14.181-108.257.amzn1.x86_64 amd64
INFO: User cache: /root/.sonar/cache
INFO: Scanner configuration file: /codebuild/output/src495061989/src/github.com/***/sonar-scanner-4.4.0.2170-linux/conf/sonar-scanner.properties
INFO: Project root configuration file: /codebuild/output/src495061989/src/github.com/***/sonar-project.properties
INFO: Analyzing on SonarCloud
INFO: Default locale: "en_US", source code encoding: "UTF-8"
INFO: Load global settings
INFO: Load global settings (done) | time=275ms
INFO: Server id: 1BD809FA-AWHW8ct9-T_TB3XqouNu
INFO: User cache: /root/.sonar/cache
INFO: Load/download plugins
INFO: Load plugins index
INFO: Load plugins index (done) | time=80ms
INFO: Load/download plugins (done) | time=16854ms
INFO: Loaded core extensions: developer-scanner
INFO: Process project properties
INFO: Execute project builders
INFO: Execute project builders (done) | time=9ms
INFO: Project key: ***
INFO: Base dir: /codebuild/output/src495061989/src/github.com/***
INFO: Working dir: /codebuild/output/src495061989/src/github.com/***/.scannerwork
INFO: Load project settings for component key: '***'
INFO: Load project settings for component key: '***' (done) | time=153ms
INFO: Found an active CI vendor: 'AWS CodeBuild'
INFO: Load project branches
INFO: Load project branches (done) | time=57ms
INFO: Check ALM binding of project '***'
INFO: Detected project binding: NOT_BOUND
INFO: Check ALM binding of project '***' (done) | time=64ms
INFO: Load project pull requests
INFO: Load project pull requests (done) | time=76ms
INFO: Load branch configuration
INFO: The base branch 'spike/test-base-branch' is not a long branch. Using its own base instead: 'master'
INFO: Load branch configuration (done) | time=3ms
INFO: Load quality profiles
INFO: Load quality profiles (done) | time=108ms
INFO: Load active rules
INFO: Load active rules (done) | time=1658ms
INFO: Exclusions based on SCM info is disabled by configuration
INFO: Organization key: ***
INFO: Pull request *** for merge into spike/test-base-branch from spike/test-pr-branch
INFO: SCM collecting changed files in the branch
INFO: SCM collecting changed files in the branch (done) | time=354ms
INFO: Indexing files...
INFO: Project configuration:
INFO: 151 files indexed
INFO: Quality profile for java: Sonar way
INFO: Quality profile for xml: Sonar way
INFO: ------------- Run sensors on module dip-serverless-motor-pmid
INFO: Load metrics repository
INFO: Load metrics repository (done) | time=52ms
WARNING: An illegal reflective access operation has occurred
WARNING: Illegal reflective access by net.sf.cglib.core.ReflectUtils$1 (file:/root/.sonar/cache/a89f1943fc75b65becd9fb4ecab8d913/sonar-tsql-plugin.jar) to method java.lang.ClassLoader.defineClass(java.lang.String,byte[],int,int,java.security.ProtectionDomain)
WARNING: Please consider reporting this to the maintainers of net.sf.cglib.core.ReflectUtils$1
WARNING: Use --illegal-access=warn to enable warnings of further illegal reflective access operations
WARNING: All illegal access operations will be denied in a future release
INFO: Sensor JavaSquidSensor [java]
INFO: Configured Java source version (sonar.java.source): 8
INFO: JavaClasspath initialization
INFO: JavaClasspath initialization (done) | time=12ms
INFO: JavaTestClasspath initialization
INFO: JavaTestClasspath initialization (done) | time=3ms
INFO: Java Main Files AST scan
INFO: 137 source files to be analyzed
INFO: 82/137 files analyzed, current file: src/main/java/com/theaa/dip/motor/pmid/dto/vo/MainVO.java
INFO: 115/137 files analyzed, current file: src/main/java/com/theaa/dip/motor/pmid/dto/DriverDTO.java
INFO: 137/137 source files have been analyzed
INFO: Java Main Files AST scan (done) | time=25550ms
INFO: Java Test Files AST scan
INFO: 0 source files to be analyzed
INFO: Java Test Files AST scan (done) | time=16ms
INFO: Java Generated Files AST scan
INFO: 0 source files to be analyzed
INFO: Java Generated Files AST scan (done) | time=1ms
INFO: Sensor JavaSquidSensor [java] (done) | time=25798ms
INFO: Sensor SonarCSS Rules [cssfamily]
INFO: No CSS, PHP, HTML or VueJS files are found in the project. CSS analysis is skipped.
INFO: Sensor SonarCSS Rules [cssfamily] (done) | time=1ms
INFO: Sensor SurefireSensor [java]
INFO: 0/0 source files have been analyzed
INFO: parsing [/codebuild/output/src495061989/src/github.com/***/target/surefire-reports]
INFO: Sensor SurefireSensor [java] (done) | time=14ms
INFO: Sensor JavaXmlSensor [java]
INFO: 1 source files to be analyzed
INFO: 0/0 source files have been analyzed
INFO: 1/1 source files have been analyzed
INFO: Sensor JavaXmlSensor [java] (done) | time=370ms
INFO: Sensor HTML [web]
INFO: Sensor HTML [web] (done) | time=4ms
INFO: Sensor XML Sensor [xml]
INFO: 1 source files to be analyzed
INFO: Sensor XML Sensor [xml] (done) | time=134ms
INFO: 1/1 source files have been analyzed
INFO: Sensor JaCoCo XML Report Importer [jacoco]
INFO: Importing 1 report(s). Turn your logs in debug mode in order to see the exhaustive list.
INFO: Sensor JaCoCo XML Report Importer [jacoco] (done) | time=154ms
INFO: Sensor ThymeLeaf template sensor [securityjavafrontend]
INFO: Sensor ThymeLeaf template sensor [securityjavafrontend] (done) | time=0ms
INFO: Sensor JavaSecuritySensor [security]
INFO: Reading type hierarchy from: /codebuild/output/src495061989/src/github.com/***/.scannerwork/ucfg2/java
INFO: Read 201 type definitions
INFO: Reading UCFGs from: /codebuild/output/src495061989/src/github.com/***/.scannerwork/ucfg2/java
INFO: 12:55:33.13453 Building Type propagation graph
INFO: 12:55:33.178034 Running Tarjan on 1963 nodes
INFO: 12:55:33.19625 Tarjan found 1963 components
INFO: 12:55:33.208266 Variable type analysis: done
INFO: 12:55:33.210644 Building Type propagation graph
INFO: 12:55:33.241283 Running Tarjan on 1963 nodes
INFO: 12:55:33.2549 Tarjan found 1963 components
INFO: 12:55:33.258726 Variable type analysis: done
INFO: Analyzing 661 ucfgs to detect vulnerabilities.
INFO: All rules entrypoints : 0 Retained UCFGs : 0
INFO: rule: S5131, entrypoints: 0
INFO: rule: S5131 done
INFO: rule: S3649, entrypoints: 0
INFO: rule: S3649 done
INFO: rule: S2076, entrypoints: 0
INFO: rule: S2076 done
INFO: rule: S2091, entrypoints: 0
INFO: rule: S2091 done
INFO: rule: S2078, entrypoints: 0
INFO: rule: S2078 done
INFO: rule: S2631, entrypoints: 0
INFO: rule: S2631 done
INFO: rule: S5135, entrypoints: 0
INFO: rule: S5135 done
INFO: rule: S2083, entrypoints: 0
INFO: rule: S2083 done
INFO: rule: S5167, entrypoints: 0
INFO: rule: S5167 done
INFO: rule: S5144, entrypoints: 0
INFO: rule: S5144 done
INFO: rule: S5145, entrypoints: 0
INFO: rule: S5145 done
INFO: rule: S5146, entrypoints: 0
INFO: rule: S5146 done
INFO: rule: S5334, entrypoints: 0
INFO: rule: S5334 done
INFO: Sensor JavaSecuritySensor [security] (done) | time=1714ms
INFO: Sensor CSharpSecuritySensor [security]
INFO: Reading type hierarchy from: /codebuild/output/src495061989/src/github.com/***/ucfg_cs2
INFO: Read 0 type definitions
INFO: Reading UCFGs from: /codebuild/output/src495061989/src/github.com/***/ucfg_cs2
INFO: No UCFGs have been included for analysis.
INFO: Sensor CSharpSecuritySensor [security] (done) | time=0ms
INFO: Sensor PhpSecuritySensor [security]
INFO: Reading type hierarchy from: /codebuild/output/src495061989/src/github.com/***/.scannerwork/ucfg2/php
INFO: Read 0 type definitions
INFO: Reading UCFGs from: /codebuild/output/src495061989/src/github.com/***/.scannerwork/ucfg2/php
INFO: No UCFGs have been included for analysis.
INFO: Sensor PhpSecuritySensor [security] (done) | time=0ms
INFO: Sensor PythonSecuritySensor [security]
INFO: Reading type hierarchy from: /codebuild/output/src495061989/src/github.com/***/.scannerwork/ucfg2/python
INFO: Read 0 type definitions
INFO: Reading UCFGs from: /codebuild/output/src495061989/src/github.com/***/.scannerwork/ucfg2/python
INFO: No UCFGs have been included for analysis.
INFO: Sensor PythonSecuritySensor [security] (done) | time=0ms
INFO: ------------- Run sensors on project
INFO: Sensor Zero Coverage Sensor
INFO: Sensor Zero Coverage Sensor (done) | time=6ms
INFO: Sensor Java CPD Block Indexer
INFO: Sensor Java CPD Block Indexer (done) | time=304ms
INFO: CPD Executor 32 files had no CPD blocks
INFO: CPD Executor Calculating CPD for 105 files
INFO: CPD Executor CPD calculation finished (done) | time=36ms
INFO: SCM writing changed lines
INFO: SCM writing changed lines (done) | time=6ms
INFO: Analysis report generated in 105ms, dir size=279 KB
INFO: Analysis report compressed in 127ms, zip size=151 KB
INFO: Analysis report uploaded in 220ms
INFO: ANALYSIS SUCCESSFUL, you can find the results at: https://sonarcloud.io/dashboard?id=***&pullRequest=***
INFO: Note that you will be able to access the updated dashboard once the server has processed the submitted analysis report
INFO: More about the report processing at https://sonarcloud.io/api/ce/task?id=***
INFO: Analysis total time: 37.759 s
INFO: ------------------------------------------------------------------------
INFO: EXECUTION SUCCESS
INFO: ------------------------------------------------------------------------
INFO: Total time: 57.220s
INFO: Final Memory: 37M/127M
INFO: ------------------------------------------------------------------------
Expected
Actual