Community Edition Version 10.3 (build 82913)
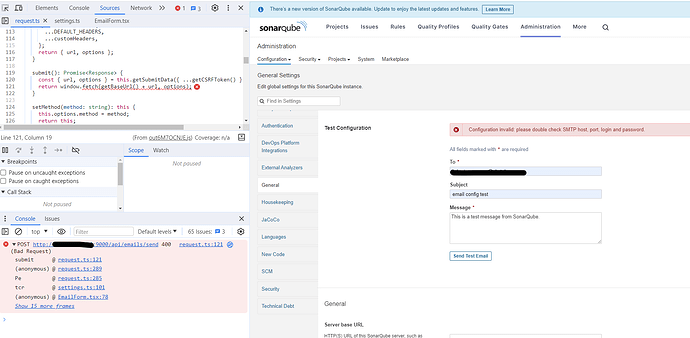
I’m trying to run “send test email” and I got host/port/user/pass error
I already set about six times all parameters, but I got the same result BAD_REQUEST
I run the command commented on stackoverflow:74181009
echo | openssl s_client -connect 1X.XXX.XX.X1:587 -starttls smtp
with this result
roberto.gamarra@mypc:~$ echo | openssl s_client -connect email-> smtp.myserver.on.amazonaws.com:123 -starttls smtp
CONNECTED(00000003)
depth=2 C = US, O = Amazon, CN = Amazon Root CA 1
verify return:1
depth=1 C = US, O = Amazon, CN = Amazon RSA 2048 M01
verify return:1
depth=0 CN = email-smtp.myserver.on.amazonaws.com
verify return:1
---
Certificate chain
0 s:CN = email-smtp.myserver.on.amazonaws.com
i:C = US, O = Amazon, CN = Amazon RSA 2048 M01
1 s:C = US, O = Amazon, CN = Amazon RSA 2048 M01
i:C = US, O = Amazon, CN = Amazon Root CA 1
2 s:C = US, O = Amazon, CN = Amazon Root CA 1
i:C = US, ST = Arizona, L = Scottsdale, O = "Starfield Technologies, Inc.", CN = Starfield Services Root Certificate Authority - G2
3 s:C = US, ST = Arizona, L = Scottsdale, O = "Starfield Technologies, Inc.", CN = Starfield Services Root Certificate Authority - G2
i:C = US, O = "Starfield Technologies, Inc.", OU = Starfield Class 2 Certification Authority
---
Server certificate
-----BEGIN CERTIFICATE-----
bla bla bla
-----END CERTIFICATE-----
subject=CN = email-smtp.myserver.on.amazonaws.com
issuer=C = US, O = Amazon, CN = Amazon RSA 2048 M01
---
No client certificate CA names sent
Peer signing digest: SHA256
Peer signature type: RSA-PSS
Server Temp Key: ECDH, P-256, 256 bits
---
SSL handshake has read 6138 bytes and written 903 bytes
Verification: OK
---
New, TLSv1.3, Cipher is TLS_AES_256_GCM_SHA384
Server public key is 2048 bit
Secure Renegotiation IS NOT supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
Early data was not sent
Verify return code: 0 (ok)
---
250 Ok
DONE
roberto.gamarra@mypc:~$
so, I can’t figure out where the real problem is
any ideas ?